Having a good command of the basic mobile applications and the cryptographic algorithm is very much important for organisations to ensure that everybody will be able to enjoy the best possible level of authentication throughout the process. Ensuring the data message integrity is very much important for the organisations to ensure that multiple details across different kinds of channels will be easily made available without any kind of doubt. The hashing algorithm is a very serious mathematical process that will be based upon playing a very critical role in public-key cryptography and will always allow the organisations to:
- Securely store all the passwords into a specific database
- Ensure a very high level of data integrity along with an indication of the data which has been altered or not.
- Helping in terms of making sure that authentication will be carried out in the best possible manner without any kind of doubt
- It will always help in making sure that everybody will be on the right track of enhancing the efficiency levels of the organisations with the implementation of perfect approaches.
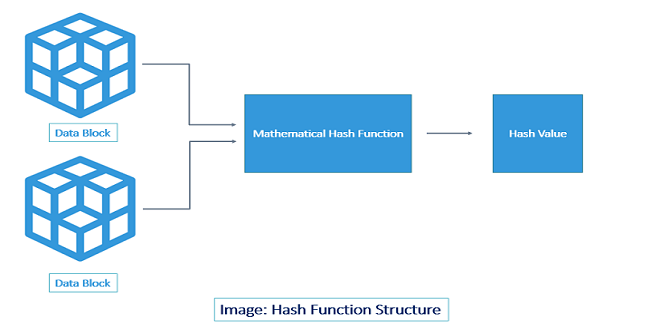
Finding out the perfect hashing algorithm with the industry is very much important so that everybody will be able to deal with things very successfully and further depending on the transmission of information in this particular case is very much advisable throughout the process. The comprehensive term of the hashing algorithm can be significantly used in terms of different scenarios depending on the context of cryptography but the definition will be a very straightforward one. This is considered to be the unique identification of any kind of piece of content so that ciphertext of the specific kind of length can be dealt with very easily and plain text of the organisations can be dealt with without any kind of problem. The very first component of this particular definition will be to make sure that there will be two pieces of content that will be having the same system so that everything will be undertaken very successfully. Hence, the hashing algorithm is considered to be the compressive option of making sure that that organisational data will be reaching the receiver in the same condition when it was left and will be completely intact without any kind of doubt.
Normally people are very much confused about the concept of encryption and hashing algorithms but it is very much important to note down that these are not the same because both of them are the best possible cryptographic functions which would be helpful in terms of facilitating the security as well as legitimate communications among the people without any kind of doubt. The very basic example of the hashing function will be to convert a plain text data input and utilisation the mathematical algorithm in such a manner that unreadable output will be easily made available throughout the process. This concept is very much versatile and will further help in creating that perfect combination that will be easily made available throughout the process so that there will be no chance of any kind of impracticality throughout the process. In this way prevention of the unintended parties will be undertaken very successfully so that there is no chance of any kind of doubt.
Some of the top-notch properties of the very strong hashing algorithm has been explained as follows:
- Speed: Hashing algorithm should always be very easily acceptable at a very reasonable speed in comparison to different kinds of situations so that computing of the values can be carried out very easily.
- Avalanche effect: This is considered to be the best possible approach of making sure the different kinds of changes will be made into the input no matter how small it will result in a massive change in the output. So, for any kind of small change in the input a comma will the two different kinds of issues in the long run which is known as the concept of apology effect and it should always be present in the whole process.
- Collision effect and resistance: The most important thing to be taken into consideration over here is the two objects collision so that there is no chance of any kind of doubt and everybody will be able to deal with the identical outputs in the whole process very successfully. The very basic and seven over here is that malicious files with artificial hashing should not be used by the users and everything should be very genuinely carried out without any kind of doubt. Hence, depending upon a good and trustworthy hashing algorithm is very much important for organisations to ensure that different kinds of conditions will be easily fulfilled throughout the process without any kind of issue.
- The pre-image resistance: This particular idea will be always making sure that everything will be invisible in terms of reversing the hash value to recover the original input clean text message so that overall goals are very easily achieved and everything will be reversible without any kind of doubt.
- Determinism: The hashing algorithm should always be deterministic in the approaches so that everybody will be able to deal with the things very successfully and everything to be carried out in an identical size regardless of the size of input which the people have started over here. This concept will always help in making sure that hashing of the single sentence will be very much successful in terms of fulfilling different kinds of purposes and overall goals will be significantly achieved without any kind of doubt.
Hence, it is very much important for the organisations to depend on that particular type of hashing algorithm which is very fast in terms of speed so that overall goals are very efficiently achieved and enablement of the organisational systems will be carried out very successfully without any kind of doubt. Hence, being very much clear about the hashing algorithm is from the house of Appsealing is the perfect decision the organisations can make so that overall goals are very easily achieved and protection can be given a great boost.
 TRUTHREVIEWERS
TRUTHREVIEWERS